Millions of Internet users around the world don’t understand how trackers work, and how advertisement networks collect your data. You are handing over the personal data without your knowledge and you wouldn’t even know about it. We are covering an important factor that only ad networks and digital marketing people would know about it. We are going to tell you what browser fingerprinting is and how you can prevent it from happening in the first place.
Contents
What is Browser Fingerprinting?
Fingerprinting has three terms and they are,
- Device Fingerprint
- Machine Fingerprint
- Browser Fingerprint
Browsing Fingerprinting is a mode of information collection technique used to collect personalized data of the remote computing device. Many marketing companies, corporate, tech giants, social media apps, social media sites, and service do it nowadays. The data collection is intended for the identification of the individual of the computer or machine user.
Unfortunately, it doesn’t matter, if you have turned off “Cookies” in the browser or other programs. If you have a service on your smartphone or desktop or laptop, then it will fetch the data and send it to the main server. Personal information is used for many purposes but they want to know who you are, where you are from, and what are you doing at the moment.
You can find out about vulnerabilities at VPNOverview Tool.
We are going to look at several ways you can protect yourself from surveillance and tracking. It is important to keep yourself protected throughout the online session because they might lead to identity theft, frauds, phishing, and other threats. There are people out there, who can spend $1000 from your Credit Card, and you cannot even stop until they have done damage to you.
1. Linux Operating System
We know that none of the reviewers & experts out there suggests you do it, but if you are serious about your online safety, then you should consider adding a secondary operating system. Either Windows or macOS is not safe because they are constantly targeted by hackers, invaders, and multi-million companies for their solutions to sell in the market.
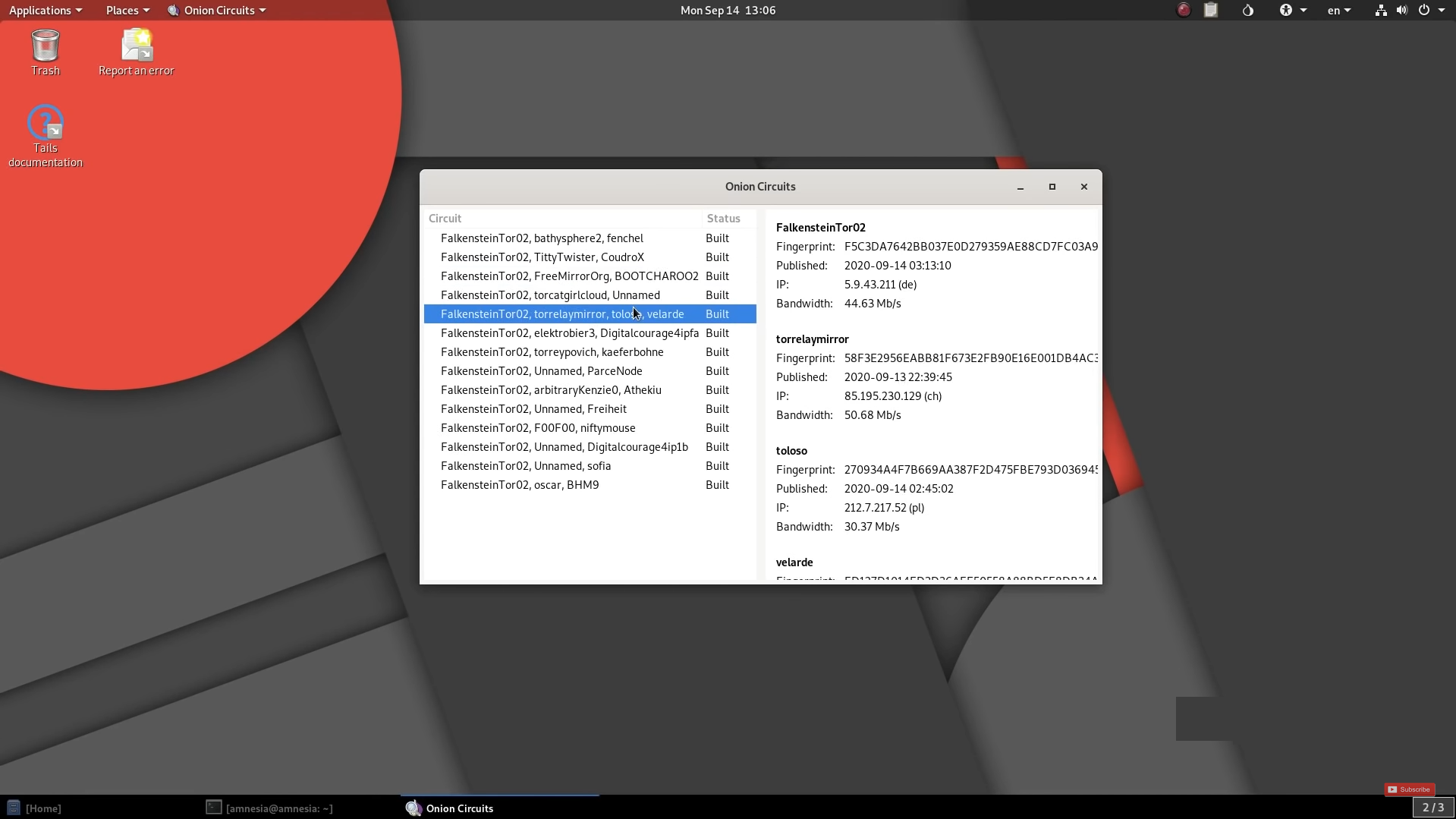
We recommend you to check out Tails OS based on Ubuntu 20.4 and Qubes OS based on Fedora. Fedora is known for its tight security and hundreds of Fortune 500 corporations have implemented it. An average consumer can try Tails OS because it is easy-to-use, and consumes fewer hardware resources.
2. Tor Browser
You may have heard about “Tor Browser” somewhere and it is a popular solution among Journalists, Army, Military, Spies, Criminals, Administrators, Developers, and Average consumers, and many other individuals. Tor is designed from the Firefox open-source browser, and they have ensured that your security is guaranteed. There’s nobody in the world, which can track remote computing device user identity and check out the snapshot below for visual explanation.
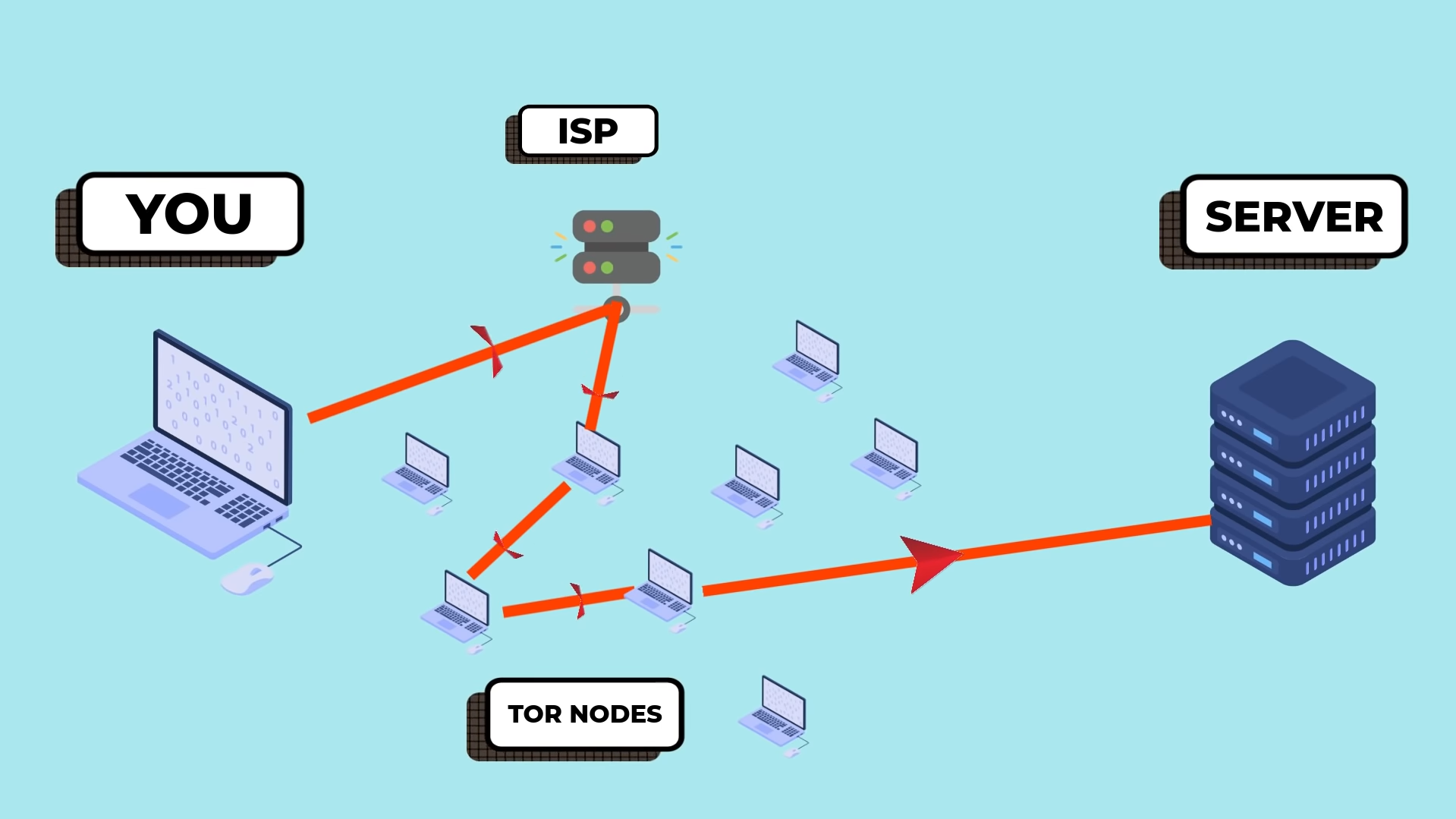
We are using Tor Browser security purposes and you can use it for browsing, unblock banned sites, access restricted content, and stay anonymous on the internet. The illustration explains that your laptop, desktop, or smartphone will connect to your Internet Service Provider, and then it will go through many active Tor Browser Nodes and then you will connect to the website. Nobody can track you because there is no way to find out the physical IP Address.
3. VPN
VPN is another massively used solution to go anonymous and keep Government surveillance, Hackers, Trackers, and Invaders away from you. VPN stands for Virtual Private Network, and there are so many solutions available online that have No Logs Policy, Military Grade Encryption, Powerful Country Data Protection Laws, and affordable yearly packages. Do not go for cheaper solutions as they don’t have power servers and make sure to check that the VPN provider is registered in a country with strong Data Law Protection. We recommend you NordVPN as they have all the necessary features and are based in Panama.
Check out NordVPN
4. Search Engine
The world of data collection started with search engines because they know so much about you. Google knows about your location, name, address, device, pages you visited, websites you visited, and years of history. If you have a Google account, then they have a year’s worth of history that the California-based search engine giant can use for personal gains.
Google developed Android OS, Mail, Google Play, Play Store, Services, and other apps. All these applications steal your information without asking you because you have agreed to the Terms & Conditions when you started using the services. We recommend you use DuckDuckGo as a primary search engine for ultimate protection from trackers.
Visit DuckDuckGo Search Engine
5. Custom Clean Android ROM
Android & iOS is a powerful mobile operating system available at your disposal. Android collects your personal information and everyone knows about it around the world. Android users can move to custom Android ROM like LineageOS, and BlissOS to get rid of Google services. We have installed LineageOS that runs on Android 10 and you no longer have to depend on Google services.
Note: Kindly conduct in-depth research on flashing a custom ROM because it can brick the device.
Bottom Line
Readers should take security & privacy into consideration before getting used to the existing technology because these multi-billion companies are stealing information. We have seen Facebook failing to protect the users from third-party companies taking advantage of the loopholes, and using it against the community.